Cybersecurity
With proven expertise and a cutting-edge cybersecurity portfolio, NTT DATA serves as your trusted advisor, guiding your business toward secure transformation.
Cybersecurity at NTT DATA – Your Partner for Secure Digital Transformation
Lead innovation through cybersecurity
NTT DATA helps create a safer digital society, enabling our clients to focus on innovation and growth. We provide clients with comprehensive protection against sophisticated threats through our worldwide resources, deep industry insights and advanced technical skills. We enable your business transformation through a coherant global approach, helping you stay ahead of evolving cyber threats and continue growth with peace of mind.
EXPLORE MORE ON WHITE PAPER
NTT DATA’s Global Cybersecurity Services
This article introduces the value that NTT DATA's Global Cybersecurity Services provide as a solution to cybersecurity threats that are advancing and becoming more sophisticated every day.
- Introduction
- Recent Cybersecurity Challenges
- Cybersecurity Capabilities of NTT DATA
- Value Provided by NTT DATA’s Global Cybersecurity Services
- Conclusions
EXPLORE MORE ON WHITE PAPER
Addressing the Emerging Challenges of OT Security in the Era of Industry 4.0
This article introduces the perspectives on IT/OT security from experts at NTT DATA.
- The challenge of IT/OT convergence
- Implications of cybersecurity under the new EU machinery regulation
- OT specific challenges
- A structured approach and progressive path to improving OT security
- Steps to improving safety in a production (quick-wins)
- Conclusions
Case Studies
Read how companies in various industries solved their challenges by partnering with NTT DATA.

Bayer Brings Its Manufacturing Operations' OT Security Up To Date
In collaboration with Bayer AG, we enhance cybersecurity for their global Pharmaceuticals Division's complex operational technology (OT) environment. Using Guardian appliances and Central Management Console from Nozomi Networks, our experts boosted asset visibility and protected critical infrastructure. We expanded asset availability across 15 major sites in globally.

Workforce Identity & Access Management Solution for Banking Services
Implementation of Identity Governance, Web Access, PAM, and Strong Authentication through the adoption of commercial security solutions for a leading Italian banking group with approximately 25,000 employees.

UNECE R156 Consulting, Process Design and Implementation
NTT DATA helped a European commercial vehicle manufacturer define and design compliance processes, roles and methods to get certified in UNECE Regulation (R156).

Design and Implementation of Vehicle Security Operation Center (V-SOC)
One of the largest suppliers and manufactures of luxury cars needed to establish a V-SOC to monitor against potential hacker attacks. NTT DATA helped design and implement it with on-board IDS systems, processes, runbooks, and more.

Design and Delivery of a Solution for Automobile Plant Security
NTT DATA assessed the security maturity of eight plants across Europe for one of the largest Japanese auto manufacturers and helped them design and implement the cyber security controls for the plants with industry security standards, such as ISA/IEC 62443 and NIST 800-82r2.

Cloud Security Migration for North American FORTUNE 200 Company
NTT DATA provided a consumer products company with architecture design of secure Azure Cloud, including AzureAD, Key Vault, Secure Configurations, and many more.

Managed Security Services for a Global Health Solutions Company
NTT DATA helped a FORTUNE 500 health solutions company implement managed security services with NTT DATA’s own Hybrid Cloud, IAM, SOC/SIEM, Threat Hunting, and more, and improve security posture with the next generation solutions.

Customer Identity and Access Management Solution for Banking Services
A leading Italian banking group needed to enable customers’ access control infrastructure in compliance with PSD2 directive, and NTT DATA helped them implement it with a Strong Customer Authentication solution, including ForgeRock Access Manager and Entrust IdentityGuard.

Network Visibility and Threat Detection in Operational Technology
NTT DATA provided a leading chemical and pharmaceutical company in Germany with operational technology threat detection solution, including architecture, site preparation, installation, training, and more with local support in more than 20 countries.
Our Services
NTT DATA provides integrated security services from strategy to operations and incident response on a global scale.
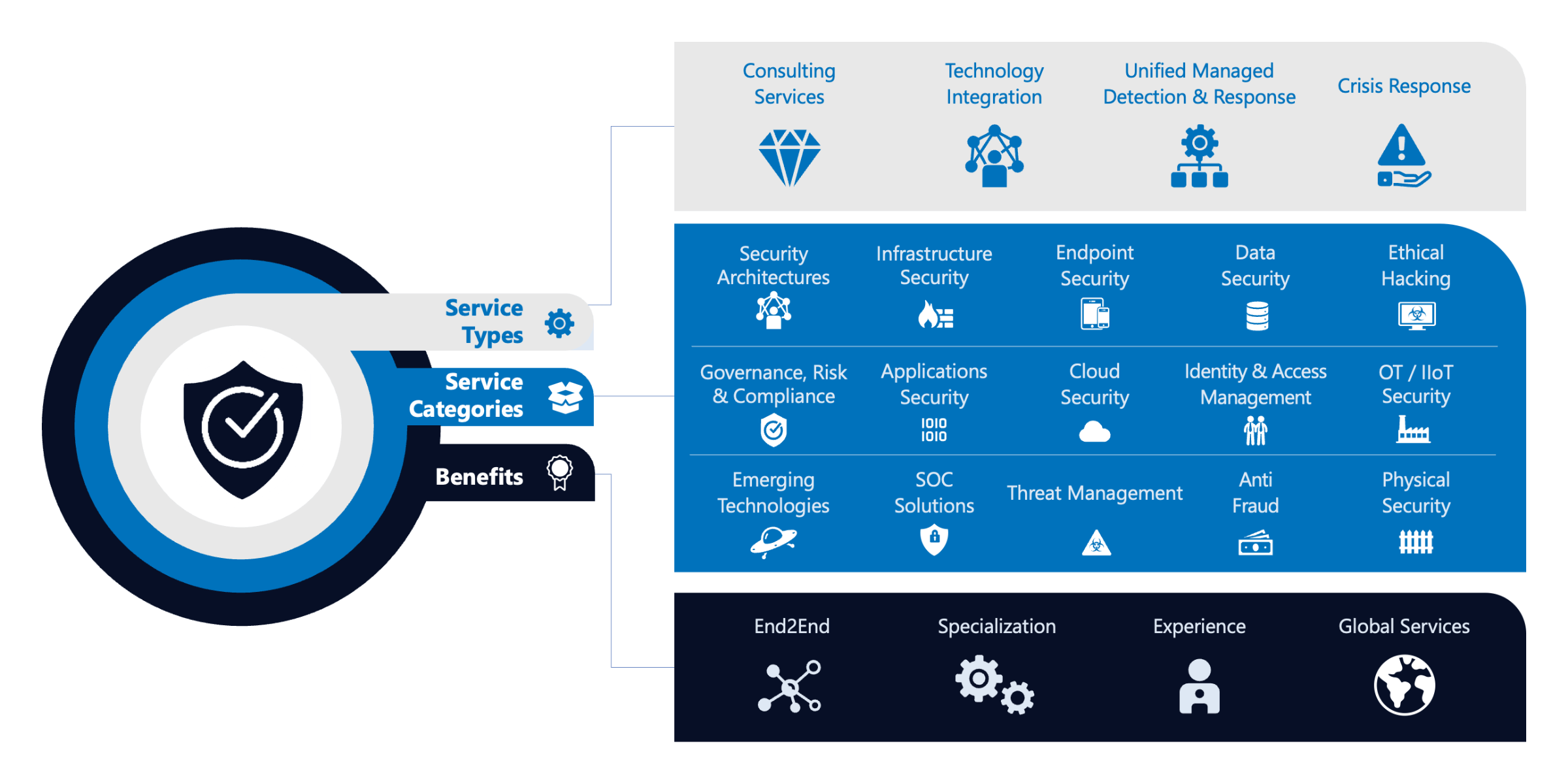
Consulting Services
Help businesses and organizations identify opportunities, solve complex problems, and design effective solutions.
Technology Integration
Set up and customize software platforms to meet the specific needs and requirements of a business or organization.
Unified Managed Detection & Response
Continuously identify, assess, classify, remediate and mitigate security weaknesses, including root-cause analysis.
Crisis Response
Fast crisis response and recovery services in case of a sudden cybersecurity incident.
Zero Trust Implementation by NTT DATA
NTT DATA has years of experience with Zero Trust security. We can help you implement a Zero Trust security model based on proven technologies that are suitable for your company by combining multiple services of our portfolio.
Zero Trust is a security model based on a principle, “never trust, always verify.” It enables companies to get rid of tedious and expensive security controls and build a more dynamic and efficient technological platform that is tailored to their customers and their business needs.

Our Partners
NTT DATA has strategic partnerships with vendors and can provide the appropriate solution to meet your requirements.











Resource Library
Explore our latest research, insights, and news on the crucial topics in cybersecurity.

BLOG: NTT DATA FOCUS
NTT DATA Shines at Europe's IT security trade fair: it-sa Expo & Congress 2024

BLOG: NTT DATA FOCUS
Strengthen your cyber resilience with extended detection and response (XDR) from NTT DATA

NEWS
NTT DATA partners with Palo Alto Networks to deliver AI-driven cloud-to-edge cybersecurity to enterprise clients

BLOG: NTT DATA FOCUS
Global Security Governance: Insights from Kirin Group's Strategic Initiatives and Approaches

GUIDE
How to deal with security risks in large language model (LLM) applications

BLOG: NTT DATA FOCUS
Part two: Improving cyber attack response capabilities with malware information sharing platform (MISP)!
-
BLOG: NTT DATA FOCUS
Improving cyber attack response capabilities with malware information sharing platform (MISP)!
-
BLOG: NTT DATA FOCUS
Participation and sponsorship of the 36th Annual FIRST Conference
-
BLOG: NTT DATA FOCUS
-
BLOG: NTT DATA FOCUS
-
BLOG: NTT DATA FOCUS
-
WHITE PAPER
-
BLOG: NTT DATA FOCUS
Security Risks of Generative AI and Countermeasures, and Its Impact on Cybersecurity
-
BLOG: NTT DATA FOCUS
-
NEWS
-
BLOG: NTT DATA FOCUS
-
BLOG: NTT DATA FOCUS
Improve Supply Chain Security through Visualization of Software Components Using SBOM
-
BLOG: NTT DATA FOCUS
NTT DATA Global Efforts to Increase Cybersecurity Professionals
-
NEWS
-
WHITE PAPER
Towards Migration to Secure Information Infrastructures Even in Quantum Computers Era (PDF: 1,6MB)
-
WHITE PAPER
-
NEWS
-
NEWS
-
BLOG: NTT DATA FOCUS
You can only protect what you know - The importance of OT environment visualization
-
BLOG
How to Adopt Modern IDS and VSOC for Your Vehicle's Security
-
INSIGHT VIDEO
Protecting Networked Vehicles Against Cyber Attacks with NTT DATA’s V-SOC
-
BLOG
-
ARTICLE
-
BLOG
Strengthening Security Programs Through a Human-Centric Focus
-
NEWS
Industry Recognition
NTT DATA has been recognized for its innovative use of technologies and solutions that help customers drive innovation. Explore the details of each recognition and award below.
-
Gartner® Recognition / 2024 *
Ranked #1 by Revenue in the 2024 Gartner Competitive Landscape: CSP Managed Security Services 2024
-
Gartner® Recognition / 2022 **
Ranked #2 by Revenue in the 2024 Market Share Analysis: Managed Security Services, Worldwide, 2022
-
Palo Alto Networks / 2024
-
Rubrik / 2024
-
Claroty / 2024
-
Google Cloud / 2023
Rising Star Award (Security)
-
Cisco / 2023
Multiple partner awards
-
CrowdStrike / 2023
Central European Technical MVP Partner Award
-
Exabeam / 2023
-
Okta / 2023
-
Palo Alto Networks / 2023
2023 SASE Partner of the Year for North America and SI Partner of the Year for EMEAL
-
Zscaler / 2023
- * Gartner, Competitive Landscape: CSP Managed Security Services, 24 April 2024.
- ** Gartner®, Market Share Analysis: Managed Security Services, Worldwide, 2022, 19 May 2023.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved. Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner's research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
Our Impact
7.5K+
Cybersecurity Professionals
NTT DATA currently employs more than 7.5K security professionals highly specialized in various industries and technologies around the world.
80+
Cybersecurity Delivery Centers
NTT DATA has more than 80 cybersecurity delivery centers worldwide and can provide solutions to meet cost and regulatory compliance requirements.
49
Security Operations Center facilities
NTT DATA have security operation centers (SOCs) globally, enabling us to support customers wherever they are in the world.
30+
Years of Cybersecurity Experience
NTT DATA has more than 30 years of cybersecurity service experience.
40%
Global Threat Intelligence
NTT DATA leverages global threat intelligence gained from analytics of over 40% of the global internet traffic in NTT backbone.
Cybersecurity Services in Your Country
We provide our cybersecurity services in the following countries. Follow the link to find out what specific services are available in your country.
NTT DATA Services
NTT DATA EMEAL
NTT Ltd.
NTT DATA

For Other Services
Select a country below to explore other services and solutions available in your country.
Quarterly Report on Global Security Trends
NTT DATA’s CSIRT (Computer Security Incident Response Team), NTTDATA-CERT, publishes a quarterly report on global security trends from its own perspective to keep the industry up-to-date with current and future cybersecurity information.
Quarterly Report on Global Security Trends: 2nd Quarter of 2023
- Featured Topic: Revisions related to cloud services in the government security common standards, FY2023 edition
- Featured Topic: Digital ID wallets
- Threat information: Cyberattack incidents targeting Microsoft Teams users
- Threat information: Escalation of cybercrime through generative AI chatbots and deepfakes
Past Reports
- 2022
RADAR Cybersecurity Magazine
NTT DATA's global cybersecurity team issues a monthly magazine. It explores the latest cybersecurity news of the month and features a feature article.
Latest Magazine: Number 97, December 2024
- Featured Topics
- Convergence of physical and logical security in modern cybersecurity
- A tale of attacks, resilience and critical lessons
- AI personality replication: challenges and opportunities
- Vulnerabilities: recently disclosed critical vulnerabilities
- Patches: recently released urgent patches
- Events: global cybersecurity events scheduled throughout the month
Past Volumes
- 2024
-
- RADAR Cybersecurity Magazine: Number 96, November 2024 (PDF: 1.1MB)
- RADAR Cybersecurity Magazine: Number 95, October 2024 (PDF: 1.3MB)
- RADAR Cybersecurity Magazine: Number 94, September 2024 (PDF: 1.8MB)
- RADAR Cybersecurity Magazine: Number 93, August 2024 (PDF: 1.2MB)
- RADAR Cybersecurity Magazine: supplement, July 2024 (PDF: 1.8MB)
- RADAR Cybersecurity Magazine: Number 92, July 2024 (PDF: 1.0MB)
- RADAR Cybersecurity Magazine: Number 91, June 2024 (PDF: 1.2MB)
- RADAR Cybersecurity Magazine: Number 90, May 2024 (PDF: 622KB)
- RADAR Cybersecurity Magazine: Number 89, April 2024 (PDF: 952KB)
- RADAR Cybersecurity Magazine: Number 88, March 2024 (PDF: 2.0MB)
- RADAR Cybersecurity Magazine: Number 87, February 2024 (PDF: 1.0MB)
- RADAR Cybersecurity Magazine: Number 86, January 2024 (PDF: 1.2MB)
- 2023
-
- RADAR Cybersecurity Magazine: Number 85, December 2023 (PDF: 926KB)
- RADAR Cybersecurity Magazine: Number 84, November 2023 (PDF: 1.0MB)
- RADAR Cybersecurity Magazine: Number 83, October 2023 (PDF: 1.2MB)
- RADAR Cybersecurity Magazine: Number 82, September 2023 (PDF: 646KB)
- RADAR Cybersecurity Magazine: Number 81, August 2023 (PDF: 644KB)
- RADAR Cybersecurity Magazine: Number 80, July 2023 (PDF: 1.1MB)
- RADAR Cybersecurity Magazine: Number 79, June 2023 (PDF: 1.1MB)
- RADAR Cybersecurity Magazine: Number 78, May 2023 (PDF: 1.1MB)
- RADAR Cybersecurity Magazine: Number 77, April 2023 (PDF: 664KB)
- RADAR Cybersecurity Magazine: Number 76, March 2023 (PDF: 1.0MB)
- RADAR Cybersecurity Magazine: Number 75, February 2023 (PDF: 1.0MB)
- RADAR Cybersecurity Magazine: Number 74, January 2023 (PDF: 1.1MB)
- 2022 and older
-
- RADAR Cybersecurity Magazine: Number 73, December 2022 (PDF: 1.0MB)
- RADAR Cybersecurity Magazine: Number 72, November 2022 (PDF: 1.1MB)
- RADAR Cybersecurity Magazine: Number 71, October 2022 (PDF: 761KB)
- RADAR Cybersecurity Magazine: Number 70, September 2022 (PDF: 679KB)
- RADAR Cybersecurity Magazine: Number 69, August 2022 (PDF: 800KB)
- RADAR Cybersecurity Magazine: Number 68, July 2022 (PDF: 1.3MB)
- RADAR Cybersecurity Magazine: Number 67, June 2022 (PDF: 730KB)
- RADAR Cybersecurity Magazine: Number 66, May 2022 (PDF: 6.7MB)
- RADAR Cybersecurity Magazine: Number 65, April 2022 (PDF: 7.1MB)
- RADAR Cybersecurity Magazine: Number 64, March 2022 (PDF: 6.9MB)
- RADAR Cybersecurity Magazine: Number 63, February 2022 (PDF: 7.1MB)
- RADAR Cybersecurity Magazine: Number 62, January 2022 (PDF: 8.0MB)
Cybersecurity Community Involvement
NTT DATA works with various organizations to contribute to the development of talents and technologies for the next generation of cybersecurity professionals in order to build a safe and secure world.

ISACA values NTT DATA’s work within the cybersecurity community. NTT DATA’s support for talent enablement and diversity in cybersecurity education/careers through OneInTech helps us prepare the generation of today for the problems of tomorrow.
— ISACA Representative

Working groups are the foundation of the way that we solve cybersecurity challenges. The research from NTT DATA, Marymount University and CSA enriches our understanding of the existing landscape of risks, defenses, attacks, and adversaries. CSA values the partnership, research and contributions by NTT DATA to the community on cloud security.
— Jim Reavis, Co-founder and CEO, Cloud Security Alliance

Established in 1990, FIRST is an organization predominantly made up of CSIRTs globally. They aim to unite incident response and security teams worldwide to ensure a safer internet for everyone. Since 2011, NTT DATA has been affiliated with FIRST attending meetings, including the Annual FIRST Conferences and the Technical Colloquiums consistently, as well as supporting the organization through sponsorship and speakers.

The Trusted Introducer was established by the European CERT community in 2000 to address common needs and build a service infrastructure providing vital support for all security and incident response teams.

As long-standing CREST members, NTT DATA has demonstrated a firm commitment to high-quality service delivery and shares in our collective mission, to build trust in the digital world.
— Jonathan Armstrong, Head of Accreditation, CREST (International)